“Reality Is Broken: Why Games Make Us Better and How They Can Change the World” by Jane McGonigal
Amazing. A fresh and new perspective on everything!
“Reality Is Broken: Why Games Make Us Better and How They Can Change the World” by Jane McGonigal
Amazing. A fresh and new perspective on everything!
In my first post, i wrote about how the Kinect was hacked and reverse-engineered. The Fluid Interfaces group over at MIT created DepthJS to let them surf the net by having the Kinect recognize certain gestures and motions.
After purchasing my own Kinect and downloading the source code from https://github.com/doug/depthjs, i realized there weren’t any good documentation on installation and setup.
Note: This is only for Mac OS X + Chrome. There are other versions for Windows.
Therefore, i have this post.
chrome://extensions
Make sure the Kinect is plugged in and refresh Chrome. You also need to be at a certain distance because if you’re too close, it won’t work. Once you see the DepthJS icon in the upper right of your Chrome browser, just stick out your hand and start navigating around!
Here’s what i saw:
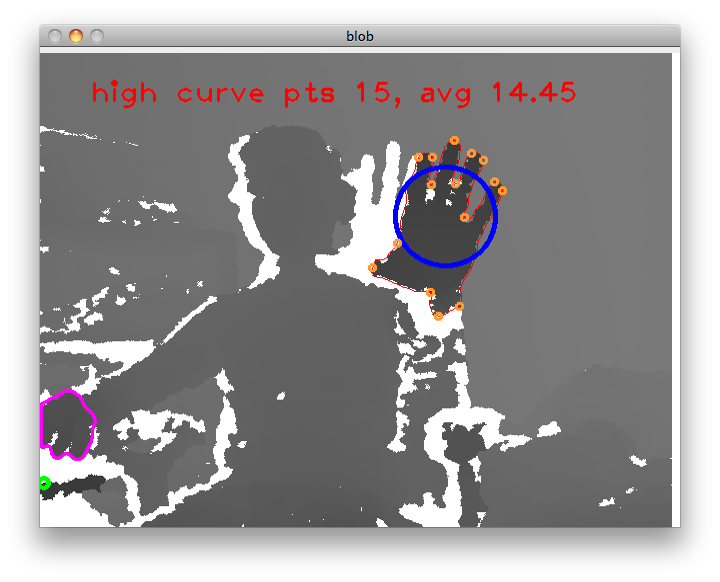 Notice how it detects my primary and secondary hands. Pretty neat! Go computer vision!
Notice how it detects my primary and secondary hands. Pretty neat! Go computer vision!
It’s been only 1 hour since i set this all up. I only managed to open links, but can’t get scrolling up/down to work despite my large hand motions. More on this later. Hopefully i’ll get up to speed and start contributing to OpenKinect and/or DepthJS in any way.
I am approximately 75% done overhauling my new website. Integrating WordPress into my current theme was tedious, but I learned alot about the code underneath. Last few things i need to do is build a new photo gallery and build some individual project pages for my portfolio. And. Then. I’m. Done.
And here’s an evolution of my previous webpages. You’ll see the huge improvements over time!
And it’s time for a new picture. In other news, i’m also taking courses at Cal Poly Pomona to kill time. I’m also working on iPhone and Ruby on Rails projects too. Cheers for now. I will update more later!
01110000 00111001 00110000 01111000 – day 3: done
On another note, i’ve been playing with Fermat’s Little Theorem. His Theorem is a way to determine if a number, N, is a prime without factoring.
Fermat’s Little Theorem:
if p is prime, then for every 1 ≤ a < p, then a^(p – 1) ≡ 1 (mod p)
I tested this by writing some code in Python:
#Fermat’s Little Theorem in Python
from math import exp
import random
number = input("Give me a number: ")
num = int(number)
a = random.randint(1,num-1)
b = a**(num-1)
if (b % num) == 1:
print("We have a prime!")
else:
print("Sorry, not a prime!")
#End of code
Of course, in math theory, there are some numbers that still pass this test, known as Carmichael Numbers. An example is 561 = 3 * 11 * 17 which fools the Fermat test. The solution is to merely run the test several times to ensure primality!
Day 2. Done
I’ll be blogging about the principles of Security Design and such! These are notes from my security course at Berkeley.
day 1 completed. Lasted only 40 minutes.